Wireless Security - WEP Encrypted WLAN
As described earlier, WEP was the first wireless "secure" model, that had authentication and encryption added. It is based on RC4 algorithm and 24 bits of Initialization Vector (IV) - this is the biggest drawback of the implementation that leads to WEP being crack-able within few minutes, as I will show in the following pages.
I will once again make use of the "LAB-test" WLAN, this type secured with WEP using the following key: "F8Be4A2c39". It is a combination of digits and letters, and it is 10 characters long – from the password strength point of view – the key is relatively strong.
The same as in last example, we will start with airodump-ng, to passively collect some information about the WLAN.
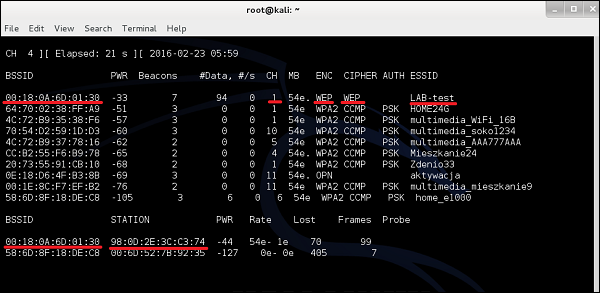
As you can see, there is "LAB-test", broadcast on channel 1 by the AP with BSSID of 00:18: 0A:6D:01:30. The encryption model is WEP, together with WEP cipher (that is based on weak RC4 algorithm). In the lower part you can see information about STATION - in fact this is the list of wireless clients connected to particular WLANs. On BSSID 00:18:0A:6D: 01:30 (it is our LAB-test), we have 98: 0D:2E: 3C:C3:74 (And guess what is that? Yes, it is my smartphone).
The next step that we need to conduct is to collect data packets exchanged over the air by this client. As you remember, data packets contain IV vector included. If we would collect enough data packets with IVs, we will finally get to the point where we have a set of weak IV vectors - it will allow us to derive the WEP password. So let's go! First we will use already knows utility airodump-ng to sniff the wireless communication for particular BSSID (BSSID of the LAB-test).
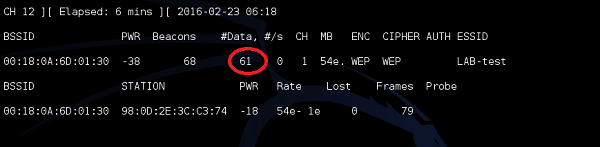
As you can see, as the traffic is flowing, the number of collected data packets is growing. At that point we have 61 data packets, and it is wise to have around 25000 at least!
After few minutes, then the counter reaches at least 25000, we can try to derive a key using the tool aircrack-ng.
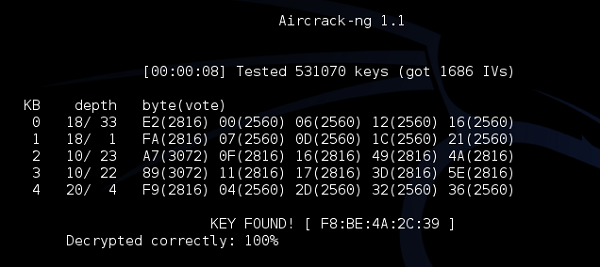
As you can see, just by passively listening to the network (and collecting enough data packets), we were able to crack the WEP encryption and derive the key. Now you have a free way to access the wireless network and use the internet.
No comments:
Post a Comment