Pentesting Unencrypted WLAN
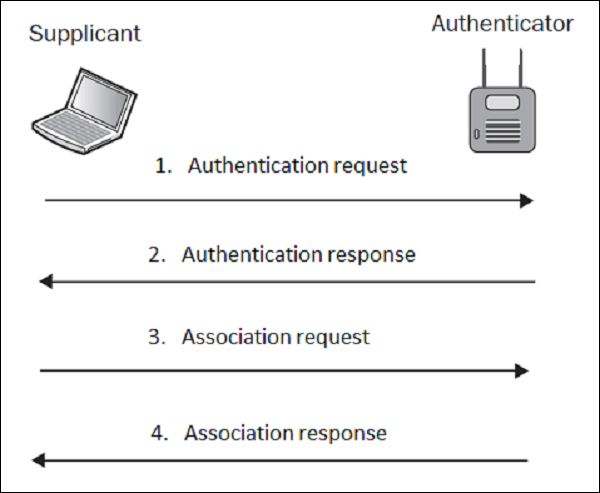
When using unencrypted WLAN (Open Authentication), your wireless network is not protected in any way. Everyone, who is located in the surrounding of the AP and can hear a signal, can join and use the network. The whole authentication process is very simplified and consists of authentication/association exchanges as shown below −
In the lab setup, I have prepared a WLAN with SSID of "LAB-test" with open authentication. As an attacker, you first need to make some passive scanning to detect such a network, so let's do it! In the first step, I will enable my wireless card and create a WLAN monitoring interface, using airmon-ng utility.
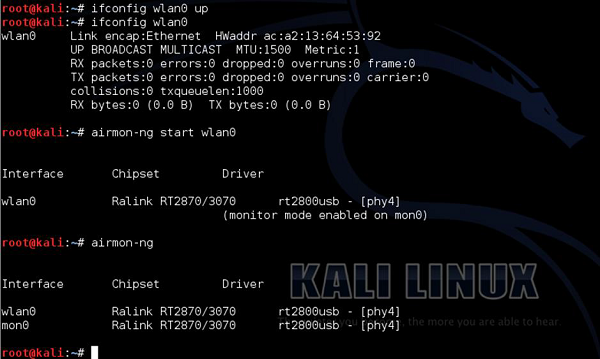
The next step it to check the WLANs that are heard by the wireless card using "airmon-ng mon0".
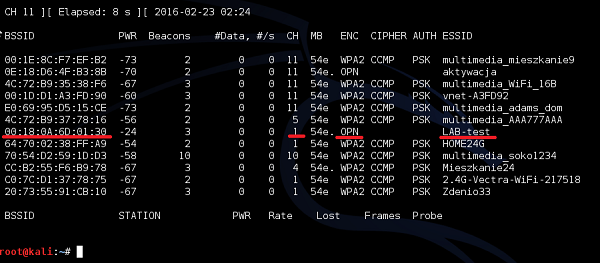
My wireless card was able to see the "LAB-test" SSID on channel 1, broadcasted by AP with MAC address (BSSID) of 00:18: 0A:6D:01:30. Under encryption column, you can see the letter "OPN" – it means that there is Open Authentication (in fact, it means no authentication at all).
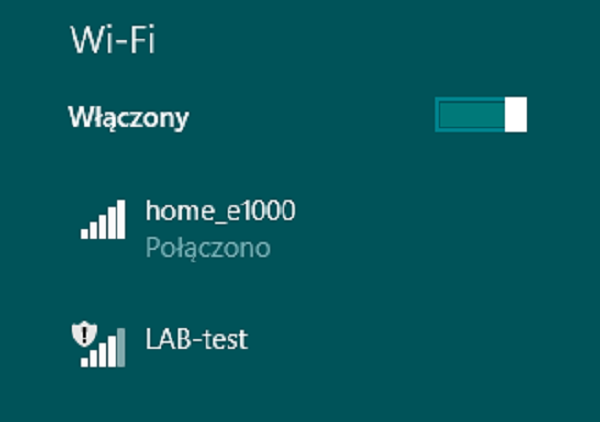
On the Windows PC, the WLAN that has Open Authentication is marked with exclamation mark as a warning of unsecure WLAN environment, as shown below (comparing to the lack of additional sign next to protected WLANs) −
We can try to simulate if the wireless client would be able to connect to this SSID. We can make it using aireplay-ng utility.
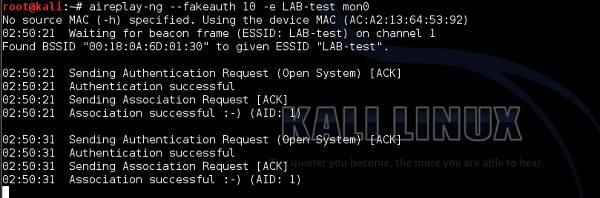
As you can see, the authentication and association process went smooth, and any wireless client is able to join the network.
The only mechanism that you can use to improve a security of this unsecure environment is to implement MAC filtering. This feature was already described earlier, so I will jump directly to practice.
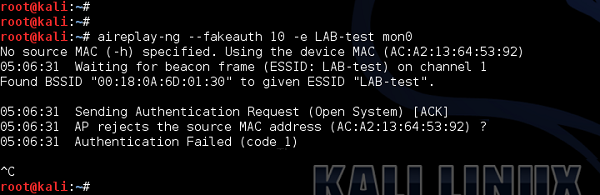
On the AP itself, I will implement a MAC filter, allowing only a client with MAC address of 98:0d: 2E:3C:C3:74 to be able to join the wireless network (this is my smartphone).
Then, when I repeat the authentication process using aireplay-ng, and this time it fails.
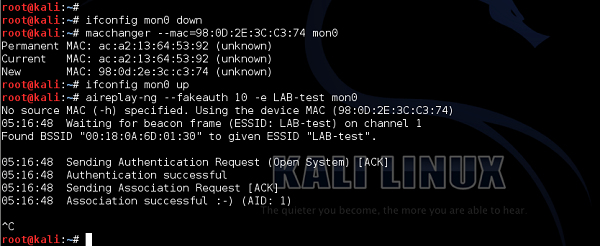
After I change the MAC address of the mon0 interface to the one that my smartphone has - I got successful authentication again.
It is very unlikely, that you will meet open authentication WLAN nowadays. But it is a very good to be aware of all those older deployment types as well.
No comments:
Post a Comment