Wireless Security Wi-Fi Authentication Modes
In this chapter, we will briefly go through the possible authentication schemes that are used in the wireless deployments. They are: Open Authentication and Pre-Shared Key (PSK)-based authentication. The former one is based on EAP frames to derive dynamic keys.
Open Authentication
The term Open Authentication is itself very misleading. It suggests, that some kind of authentication is in place, but in fact, the authentication process in this scheme is more like formal step, rather than authentication mechanism. The process looks like how it is shown in the following diagram −
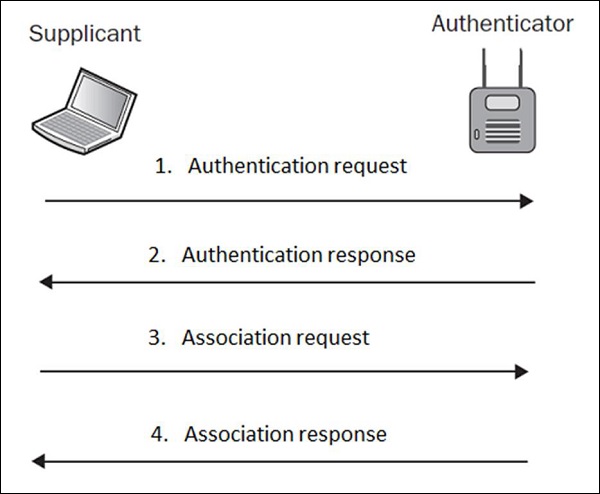
In plain English, what this exchange is saying is that, in authentication request the wireless client (supplicant) is saying "Hi AP, I would like to authenticate" and authentication response from the AP is stating "OK, here you go". Do you see any kind of security in this setup? Neither do I…
That is why, Open Authentication should be never used, since it simply allows any client to authenticate to the network, without the right security check.
EAP-based 4-way handshake (with WPA/WPA2)
When a wireless client authenticates to the AP, both of them go through the 4 step authentication process called 4-way handshake. During those message exchanges, the shared password is derived between AP and wireless client, without being transmitted in any of those EAP messages.
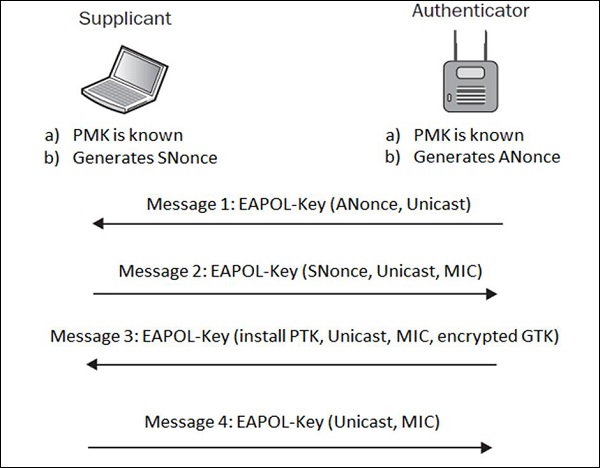
The Pairwise Master Key (PMK) is something a hacker would like to collect, in order to break the network encryption scheme. PMK is only known to the Supplicant and Authenticator, but is not shared anywhere in transit.
HOWEVER, the session keys are, and they are the combination of ANonce, SNonce, PMK, MAC addresses of Supplicant and Authenticator. We may write that relation, as the mathematical formula −
Sessions_keys = f(ANonce, SNonce, PMK, A_MAC, S_MAC).
In order to derive a PMK from that equation, one would have to break AES/RC4 (depending whether WPA2 or WPA is used). It is not that easy as the only practical approach is to perform a brute-force or dictionary attack (assuming you have a really good dictionary).
It is definitely a recommended authentication approach to use, and definitely safer than using Open Authentication.
Wi-Fi Chalking
Wi-Fi chalking was a very funny concept in the history of wireless LAN history, mainly used in the USA. The main idea was to mark the places, where open-authentication or WLANs with weak authentication were implemented. By doing that, everyone who finds out this sign somewhere on the wall or ground, written with a chalk, then he can log in to the Wi-Fi system without authentication. Smart, right?
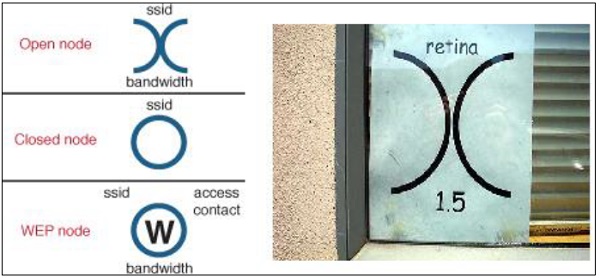
You may just ask yourself - why chalk and not some kind of marker, spray or other more permanent way of marking? The answer is simple and comes from criminal law - writing with chalk was not considered as an act of vandalism.
No comments:
Post a Comment