Wireless Security - Integrity Attacks
Integrity of the information is a characteristic that ensures that data was not tampered, when going from point A to point B over the network (either wireless or wired). When speaking about wireless communication, 802.11 radios can be overheard by any 3rd party on the same frequency channel. A simple type of attack against integrity of the information is illustrated in the following diagram −
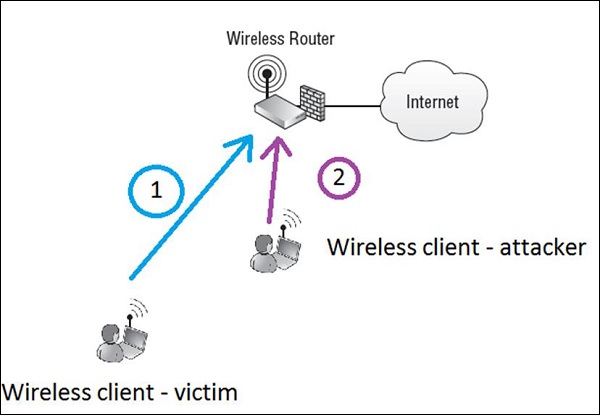
Let's imagine that legitimate wireless client called victim (Step 1) is writing an e-mail to the friend (e-mail will go to the internet), asking for money return of 1000$ and putting bank account number in the e-mail.
Assuming the information is not well encrypted (or attacker broke the encryption and have the chance of reading everything in clear text), wireless attacker (Step 2) reads the whole packet flowing in the air to the AP. The attacker modifies a message by swapping the bank account number to its own and re-inject a message back to the air, to go to the internet via the AP.
In that situation, if there are no integrity checks that would detect a change in the content of the message - the recipient would get a message with a modified bank account number. Probably, the situation described would be extremely hard to implement in real life, since all the tools like mail exchange, are secure against those types of attacks (via proper encryption and message integrity checks), it perfectly shows the concept of the attack.
There are 2 main counter-measures against this type of an integrity attack − encryption (so that attacker would not be able to read the message at all) and Message Integrity Codes (MICs) that are basically hashing function like MD5 or SHA1 that take a footprint of the whole message and create a hash of 128 bits (MD5) or 160 bits (SHA1). Anytime, there is a change in the packet content, the hash value would also change, resulting in message being denied (already by wireless router).
No comments:
Post a Comment