Wireless Security - Client Misassociation
You may have already experienced the situation, that when you come with your PC and use wireless at home, your PC is automatically connecting to the WLAN, without any actions required from you. This is because, your laptop remembers the list of WLANs that you were connected to in the past, and stores this list in the so-called Preferred Network List (in a windows world).
A malicious hacker may use this default behavior, and bring its own wireless AP to the physical area, where you are normally using your Wi-Fi. If the signal from that AP, would be better than the one from original AP, the laptop software will mis-associate to the fake (rogue) access point provided by the hacker (thinking it is the legitimate AP, you have used in the past). These kind of attacks are very easy to perform in some big open spaces, such as airports, office environments or public areas. These kind of attacks are sometimes referred to as Honeypot AP Attacks.
Creating a fake AP does not require any physical hardware. The Linux distribution, used through all this tutorial is Kali Linux, has an internal tool called airbase-ng that can create AP with specific MAC address and WLAN name (SSID) with a single command.
Let's create a following scenario. In the past, I have used the SSID of "Airport-Guest" at one of the European airports. That way, I know that my smartphone has saved this SSID on the PNL (Preferred Network List). So I create this SSID using airbase-ng.
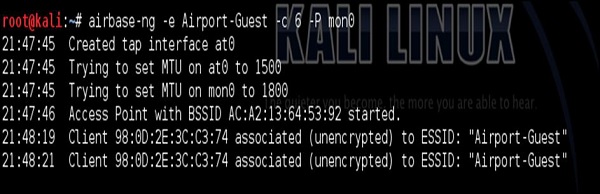
After I have created the WLAN, I have used Layer 2 DoS attack described earlier, to constantly de-authenticate my smartphone from Home_e1000 wireless network. At that point, my smartphone detects the other SSID (Airport-Guest) with a very good link quality, so it connects automatically to it.
This is something you see in the dump above starting from 21:48:19. At that point, we are in the good situation to perform some additional attacks having this initial connection. It can be either a man in the middle attack, to forward all the wireless traffic via attacker's PC (attacking integrity and confidentiality of the traffic exchange. Or you may connect back from the attacker's PC directly to smartphone by exploiting some vulnerabilities using Metasploit Framework... There is a plethora of possible ways forward.
No comments:
Post a Comment