Wireless Security - Break an Encryption
In this chapter, we will see how to break WEP and WPA encryptions. Let’s start with WEP encryption.
How to Break WEP Encryption?
There are many possible tools that one can use to crack WEP, but all of the approaches follow the same idea and order of steps.
Assuming that you have found your target network, you do as follows −
- Collect (sniff) WEP encrypted packets flying over the air. This step may be performed using a Linux tool called "airodump-ng".
- When enough packets are collected (you have collected a set of frames with duplicate IV vector), you try to crack the network using a tool called "aircrack-ng".
On a highly congested network, the above mentioned two steps can take around 5-10 minutes or even less. It is that easy! The detailed step by step guide for hacking WEP will be shown under the topic of "Pen Testing WEP Encrypted WLAN ".
How to Break WPA Encryption?
The way to break a WPA encryption has a slightly different approach. Wireless frames using WPA, are using TKIP encryption that still uses the concept of IV and RC4 algorithm, however it is modified in order to be more secure. TKIP modifies WEP with the following pointers −
- It uses temporal, dynamically created keys instead of static ones used by WEP.
- It uses sequencing to defend against replay and injection attacks.
- It uses an advanced key mixing algorithm in order to defeat IV collisions and weak-key attacks in WEP.
- It introduces Enhanced Data Integrity (EDI) to defeat bit-flipping attack possible in WEP.
Taking all of these points into account, it makes WPA standard computationally not-possible to crack (it does not say it is not possible, but it may take reasonably a very long time, assuming you have advanced resources for breaking the algorithm). Authentication used in WPA standard has also advanced in respect to one used in WEP. WPA uses 802.1x (EAP-based authentication) for authentication of the clients. In fact, this is the only weak point, where you may try your chances for breaking the WPA (and WPA2 in fact).
WPA and WPA2 standards supports two types of authentications - Pre-Shared Key (PSK) and true 802.1x based on external authentication server. When using 802.1x authentication - it is simply not possible to break the password; it is only doable where local PSK mode is used. Just as a side-note - all the enterprise wireless deployments, they use true 802.1x authentication, based on the external RADIUS server, therefore, your only possible target might be very small businesses or home networks.
One more remark is that, PSK used for protecting WPA/WPA2 must be reasonably short in size (max 10 characters - in opposite to 64 characters allowed as max length), if you have the intention to break it. The reason for that requirement is that, PSK is only transmitted once (not in clear text) between wireless client and the AP during the initial 4-way handshake, and the only way to derive the original key from those packets is by brute-forcing or using a good dictionary.
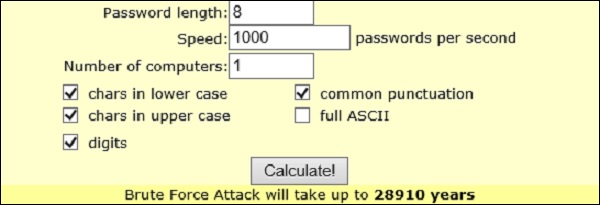
There is a pretty nice online calculator that can estimate the time it would take to brute-force the PSK - http://lastbit.com/pswcalc.asp. Assuming that you have 1 PC that can try 1000 password per second (composed of lower-case, upper-case, digits and common punctuations) it would take 28910 years to break the password (as maximum of course, if you are lucky it might take a few hours).
The general process of breaking a WPA/WPA2 encryption (only when they use PSK) is as follows −
- Collect (sniff) wireless packets flying over the air. This step may be performed using the Linux tool called "airodump-ng".
- While packets are being collected, you should de-authenticate the current clients. By doing that, you are getting to the situation, when the client would need to authenticate again in order to use a Wi-Fi network. This is exactly what you wanted! By doing this, you prepare a good environment to sniff a wireless user authenticating to the network. You can use Linux based tool "aireplay-ng" to de-authenticate the current wireless clients.
- As you have a 4-way handshake sniffed (and saved in the dump file), you can once again use "aircrack-ng" to crack the PSK. In this step, you have to reference a dictionary file containing all the combinations of the password, that aircrack-ng tool will use. That is why, a good dictionary file is a most important element here.
Detailed step-by-step hacking of WPA/WPA2 networks will be shown under the topic " Pen Testing WPA/WPA2 Encrypted WLAN ".
How to Defend Against WPA Cracking?
I have a feeling, that after going through the last sections of this tutorial, you will already have some idea, what should be done in order to make WPA cracking not possible (or rather say: impossible within a reasonable period of time). Following are some pointers of the best practices for securing your home/small business wireless network −
- If there is a chance for that, use WPA2 instead of WPA. It has a direct impact on the encryption scheme used by a suite. AES (used by WPA2) is much more safe than TKIP (used by WPA).
- As you saw earlier, the only way to break WPA/WPA2 is by sniffing the authentication 4-way handshake and brute-force the PSK. To make it computationally impossible, use a password of at least 10 characters composed of random combination (not any plain word that you can meet in any dictionary) of lower case, upper case, special characters and digits.
- Disable Wi-Fi Protected Setup (WPS) - WPS is one of the "cool features" invented to make connecting new wireless clients to the network much more easy - just by putting a special 8-digit PIN number of the AP. This 8-digit is a very short work for a brute-force attack, and also this 8-digit may be found on the back of the AP box itself. Give yourself a try and have a look at your home router - do you see WPS PIN on the back? Do you have WPS feature enabled on your home router?

No comments:
Post a Comment