Wireless Security - Bluetooth Hacking Tools
On the internet, there are tens of hundreds of tools already made, that will facilitate Bluetooth hacking. For sure, it is not possible to be aware and know all of them, and in my opinion - the fundamental knowledge that is needed is to know the tools used for a reconnaissance phase.
When you pass through this stage, you have to decide what is the goal of hacking approach to inject some files? Or to steal data? Or to execute malicious malware? Depending on your direction, there are a different set of tools you should use.
Therefore, concentrating on the reconnaissance (discovery phase) and internal kali Bluetooth hacking tools would be our goal for this chapter.
hciconfig
This hciconfig is the main Linux command line utility used for interacting with Bluetooth device (Bluetooth dongle). If you know Linux, you may already see the reference to other tools like ifconfig or iwconfig.
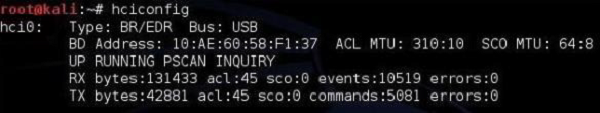
The information you get read from hciconfig output are −
- The name of the interface - "hci0".
- How it is connected to a PC (either via a USB or built-in) here it is the USB dongle.
- MAC address of the Bluetooth dongle - 10:AE:60:58:F1:37.
- It is currently running (UP flag) and you can see received (RX) and transmitted (TX) packets.
hcitool
This hcitool is a very powerful CLI tool implemented in kali Linux that allows a user to interface with the Bluetooth stack. It is also a great tool that you can use in your own scripts.
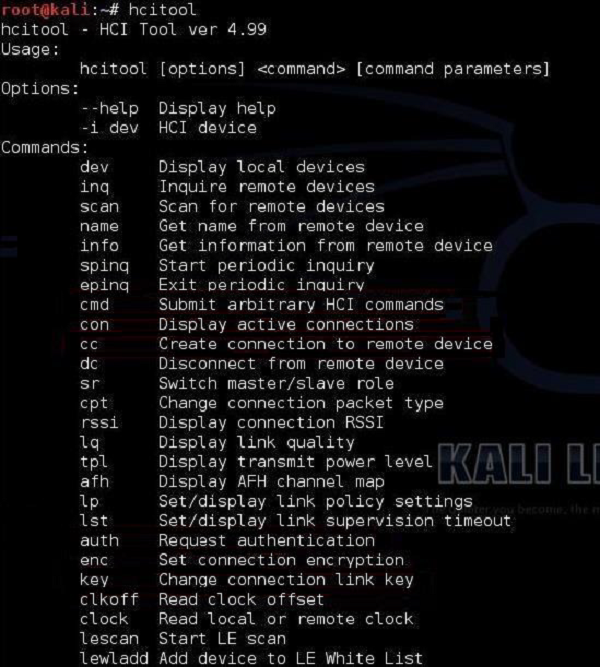
The most common options of this hcitool are scan and inq.
An hcitool scan will allow you to find Bluetooth devices that are sending out their discovery beacons (something like 802.11 beacon frames sent out by AP).

As you can see that in the neighborhood, two Bluetooth enabled devices were sending out beacon frames to inform about their readiness to accept Bluetooth connections. You can try to find more Bluetooth information about those two by using the hcitool inq.
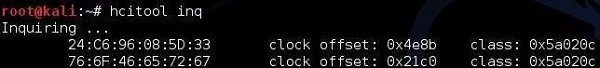
What this output says is that the following devices belong to class 0x5a020c(you can find the description and mapping of the classes here − (https://www.bluetooth.com/specifications/assigned-numbers/service-discovery )
sdptool
Kali Linux also has a built-in tool for performing Service Discovery (SDP). It allows you to enumerate all the services running on the Bluetooth device.
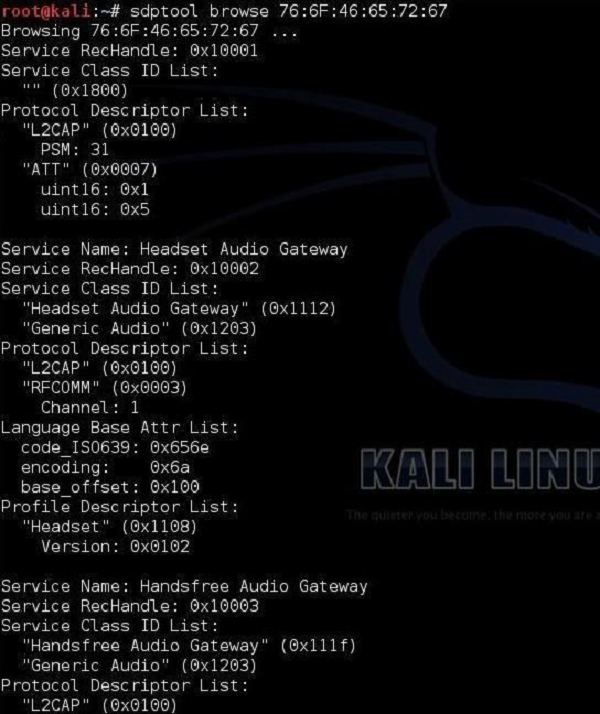
l2ping
All of us know the ping utility from the IP world that is used to check the connectivity between IP nodes using the ICMP protocol. The Bluetooth world has its own equivalent called l2ping. This discovery tool, allows the user to check whether a particular device is within the range and is reachable for Bluetooth communication.
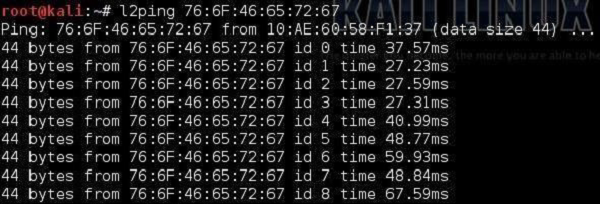
Those were the basic tools that will allow you to play with Bluetooth technology and make very good reconnaissance of its operation. The tool that was mentioned earlier hcitool, this is the one you should spend some time with, if you want to really develop in this area of Bluetooth penetration testing.
No comments:
Post a Comment